New round of targeted phishing emails attempt to gather UA log-in credentials
May 25, 2021
A new round of targeted phishing emails was delivered to UA inboxes Sunday. You may
have received it. These phishing emails have appeared too good to be true (“Employee
Performance Bonus!”) or they may have instructed you to act right away. These emails
appear more convincing because they seem to come from known UA accounts. Unfortunately,
these are phishing emails and you should not enter your UA credentials on the fake UAONLINE page.
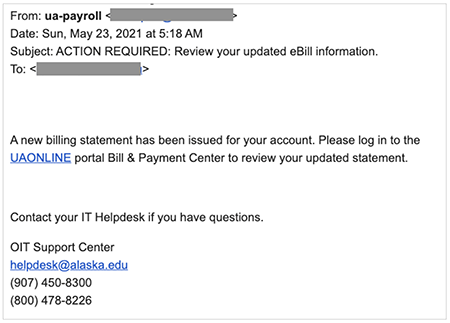
As with previous phishing attempts, when you hover over/preview the UAONLINE link in the email, you will notice it is not directing you to an alaska.edu link, but to a fraudulent URL that hosts a convincing replica of our SSO page:
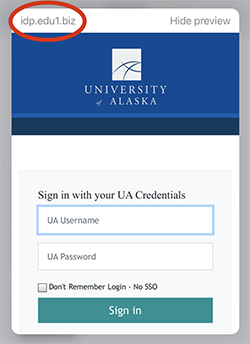
This phish is aimed at gaining access to your UA credentials. The moment you log into the fraudulent SSO form you see a blank page, but the attacker has captured your login and password. Unless you have Multi-Factor Authentication (MFA) enabled, the attacker then has everything he or she needs to access your UA information, including ELMO and UAOnline.
If you responded to this or a similar email and followed the link and entered your password, please immediately visit ELMO (elmo.alaska.edu) to change your password.
You can help protect yourself from these types of attacks by enabling Multi-Factor Authentication on your account. Multi-Factor Authentication adds an extra layer of security between your information and your credentials.
Modern scammers are exceptionally clever in finding ways to capture sensitive information
from targeted users. To learn more about protecting yourself from phishing attempts
go to https://alaska.edu/
